'Intimidation Diversity' Spreading in Ransomware Groups
iStock.com/style-photography
Ransomware gangs are no longer limited to exposing data or threatening to sell it to others for ransom payment tactics and techniques. Peter McKenzie, director of incident response at Sophos, said ransomware gangs have supplemented their demands with new threats as companies have improved their data protection. "I saw a method of using stolen personal information to send an e-mail to an employee by name or make a phone call to scare the victim and demand a ransom from the employer." This kind of modus operandi represents a shift in ransomware from purely technical attacks that target systems and data to attacks that target humans," Mackenzie said.
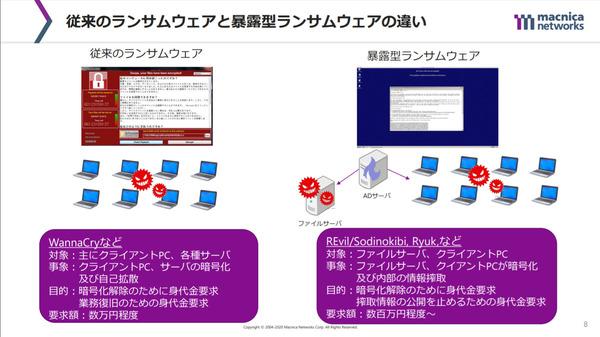
Old and new methods of ransomware attacks
Data theft and exposure are the most common methods. If you're hit by a ransomware attack, it's reasonable to assume that you've probably suffered a data breach first. An investigation conducted by Sophos found that the Conti attack on a transportation and logistics company stole data, including the results of traffic accident investigations, such as driver names and fatalities. The second most common method is the aforementioned method of threatening to "disclose personal information" by email or phone. This is commonly used by Conti, Maze, REvil and SunCrypt. The third method used is related to the second. It is a method of contacting individuals and companies related to the information that the victim had and threatening to persuade the victim to pay the ransom. This is often used by Cl0p and REvil. The fourth method is to silence the victim by warning them not to report it to the authorities. Recently, there are more methods of warning not to tell the media. It was originally intended to prevent victims from seeking help from others to avoid paying the ransom. Recently, ransomware groups have tended to care about their image, he said. ] In October 2021, Conti complained that the negotiation process with JVC Kenwood had been leaked, and commented that if the negotiation process fell into the hands of the media and researchers, he would stubbornly discontinue the negotiations and disclose the obtained data. A method that has spread rapidly recently is to recruit insiders of the target in exchange for a reduced ransom to launch ransomware attacks on others. In a case investigated by Sophos, the criminals behind LockBit 2.0 posted ads with ransom demands to recruit people to attack third parties and partners of the victim companies. In addition, there are other methods that hinder the victim's IT activities in some way, causing new anxiety and increasing the possibility of paying the ransom. Reset domain administrator passwords to disable login, delete all backups, launch DDoS (distributed denial of service) attacks on targeted websites, continuously print ransom notes to office printers It has been confirmed that the act of disabling the "Even if files are encrypted, they can often be restored from backups, so attacks are no longer limited to encryption. This shows how important a defense-in-depth approach is." (Mr. Mackenzie)
TechTarget Japan